Companies have been dealing with security for decades, but the escalate of incidents and attacks like Ransomware has been proving that we are losing this war.
There was always this idea of prevent/detect it on upper layers, like border firewalls, IDS/IPS systems which on the actual distributed environment, on-prem/cloud/edge, remote workforces, is becoming more and more challenged, specially with the use of traditional approaches/tools.
Prevent/Detect is as important as is to reduce the attack surface, no doubt if there was no vulnerability to exploit than there's nothing to worry about, right ? of course there's no such thing as 100% guarantee of security, and if someone is telling you that be suspicious (at least).
To reduce the attack surface you can implement a few disciplines like Hardening Guides and Vulnerability Management. That is one of the areas VMware can help with.
Carbon Black Cloud Workload Protection is aimed to bring Infrastructure and Security Teams together with a unified view, identifying and prioritizing vulnerabilities in your environment so you can act upon it accordingly, lets see what I'm talking about:
Workload Protection is integrated with vCenter, meaning that Infrastructure teams don't have to learn any new tool, it's already there in the environment they know and love. Also, they will have the same vulnerabilities view the security teams have.
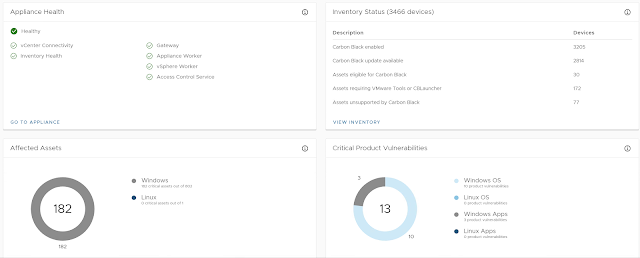
It starts with a nice Overview of your environment. You can immediately see your inventory's status, how many systems are affected, and the categorization of them.
*** Prioritization ***
It's not news that everybody is overloaded with activities, there's no way anyone of us could do everything, be on top of vulnerabilities popping up every single day, adding to that constant changes on your environment, workloads being provisioned automatically, it's really hard to keep track of all of it without proper tools. would not be nice if you could focus your efforts on what's really important ?!?
Your welcome ; )
By default, the Vulnerabilities page point you to the critical systems that need immediate attention. It's by far the greatest way of saving hours of you have to dig on the systems/vulnerabilities to understand what's critical or not.
You can make your analysis by grouping them by affected systems or by vulnerabilities. Either way, you will see the Risk Score, systems affects, and more..
The way we rank the vulnerabilities is the most innovative way in order to help you focus on what's critical.
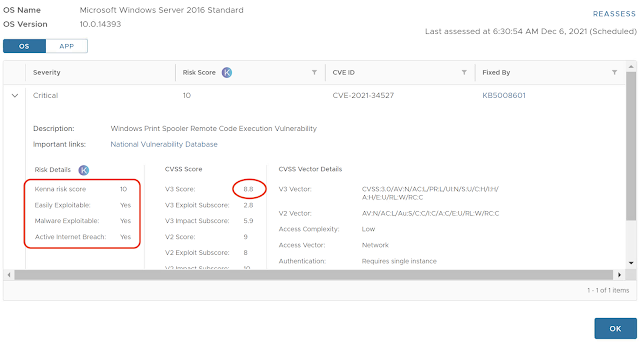
Despite the score provided by Common Vulnerability Scoring System (CVSS), you would need more information of the vulnerability, like the method of attack, likelihood of being attacked, that's where VMware in Partnership with Kenna Security come to rescue and master the risk score based on a few extra criteria
- Easily Exploitable: Is that a vulnerability easy to be exploited, have the method being recorded
- Malware Exploitable: Has this been productized/weaponized on tools or exploit kits
- Active Internet Breach: Is it presence on your location or real-time exploitation
Based on those criteria we can reassess the risk and provide you with a more realistic risk of each vulnerability, allowing you to focus on the critical ones.
*** Agentless - Scanless ***
Because we are integrated with vSphere there's no need to install and lifecycle extra agents on the Virtual Machines, we could collect all required information through VMware tools.
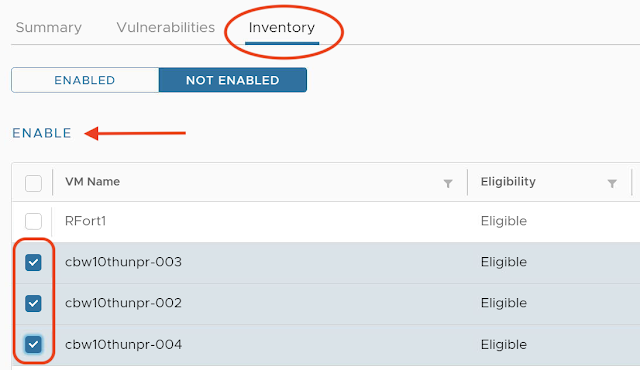
On the Inventory tab, you can select the assets that are not being monitored. To enable the collection, simply just select the VMs and hit the button ENABLE.
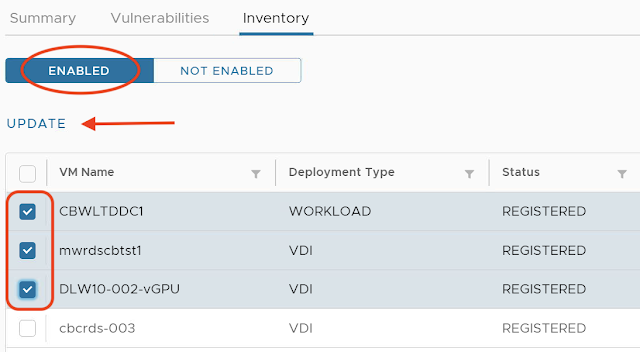
With time is common that you have to update the sensor collecting the data, a simple task with the vSphere integration.
Just select the desired assets and hit the UPDATE button.
As you can see Workload Protection is doing a fantastic job bringing together Infrastructure Team and Security Team together, but most important is to give you insights on where to focus your efforts to keep the environment safe.
Please, let me know what measurements you are using to keep the bad guys out.